At the outset, it is stated that under the Indian Law, “ Data Theft” is a misnomer. Under the Indian Law, there is no offence of “Data Theft” i.e. theft of Data.
Section 378 of the Indian Penal Code, 1860 defines Theft as follows:-
“ Theft – Whoever, intending to take dishonestly any movable property out of the possession of any person without that person’s consent, moves that property in order to such taking, is said to commit theft.”
Section 22 of I.P.C., 1860 defines “movable property” as follows:-
“The words “movable property” are intended to include corporeal property of every description, except land and things attached to the earth or permanently fastened to anything which is attached to the earth.”
Section 378, Indian Penal Code, 1860 refers to “movable property” i.e. corporeal property, and since Data by itself is intangible, it is not covered therein. Just as theft of Electricity has been made a part of the definition of Theft under Section 378 I.P.C. through a legal fiction contained in Section 39 of the Indian Electricity Act, 1910, similarly the legislature should actively consider amending the law by covering Data also under the definition of Theft. Requisite amendments should be made to the Indian Penal Code, 1860 and / or the I.T.Act, 2000 for the said purpose.
The Supreme Court of India in Avtar Singh vs State of Punjab, reported in AIR 1965 SC 666, has held as follows:-
” (6) With regard to the first reason that Section 39 of the Act extended the operation of Section 378 of the Code, it seems to us beyond question that Section 39 did not extend Section 378 in the sense of amending it or in any way altering the language used in it. Section 378, read by itself even after the enactment of Section 39, would not include a theft of electricity for electricity is not considered to be moveable property. The only way in which it can be said that Section 39 extended Section 378 is by stating that it made something which was not a theft under Section 378, a theft within the meaning of that section. It follows that if Section 39 did so, it created the offence itself and Section 378 did not do so. In this view of the matter we do not think it possible to say that the thing so made a theft and an offence, became one by virtue of Section 378”
Data as such is not movable property and the question of its theft is hence per se irregular. However, if Data is stored in a medium (CD, Floppy etc.) and such medium is stolen, it would be covered under the definition of Theft, since the medium is a movable property.
In view of the aforesaid legal position, the expression “Data Theft”, being a misnomer in law, shall not be used hereinafter and instead, the expressions “Data Crime” and “Data Criminals” shall be used.
Since Data Theft is no Theft in law, alternative legal strategies need to be explored to check, deter and punish this menace, which is rampant in the I T World, in which Data is a very valuable asset. At the same time, due to its nature, Data is extremely vulnerable to being misappropriated, copied, hacked etc. The maximum risk to Data, is from employees handling /using the same during the course of their employment and other independent contractors (Call Centres etc.) entrusted with the Data to carry out specific tasks / assignments. The most common modus- operandi adopted by Data Criminals is to sell the same to competitors, who benefit through reduction in effort, time and costs of building their own Data Base or buying the same from the market.
The Data Criminal can be effectively dealt with under various provisions of the Indian Penal Code, 1860, I.T. Act, 2000 & The Copyright Act , 1957. In so far as the Data Criminals from amongst the employees and other independent contractors are concerned, the offence of Criminal Breach of Trust, defined and made punishable under Sections 405 – 409 of I.P.C., 1860 need to be activated and the Agreement(s) with employees and independent contractors should be drafted keeping in view the said provisions of I.P.C.
Indian Penal Code, 1860:
Section 405 defines Criminal Breach of Trust as follows:-
“Criminal Breach of Trust.- Whoever, being in any manner entrusted with property, or with any dominion over property, dishonestly misappropriates or converts to his own use that property, or dishonestly uses or disposes of that property in violation of any direction of law prescribing the mode in which such trust is to be discharged, or of any legal contract, express or implied, which he has made touching the discharge of such trust, or willfully suffers any other person so to do, commits ‘criminal breach of trust’ ”.
Section 405 refers to “property” and not “movable property”, hence, the word “property” is not restrictive. Therefore, Data would be covered within the ambit of “property” in Section 405 I.P.C. The Supreme Court in R.K. Dalmia vs Delhi Administration, reported in AIR 1962 SC 1821, has held that the word “property” could not be restricted to movable property especially when it is used without any qualifications in Section 405 or other Sections of the Penal Code. The Hon’ble Supreme Court inter-alia stated as follows:-
“(57) The case law, therefore, is more in favour of the wider meaning being given to the word ‘property’ in sections where the word is not qualified by any other expression like ‘movable’.”
“(58)……That a debt is property is, we think, clear. It is a chose in action and is heritable and assignable and it is treated as property in India under the ‘Transfer of Property Act which calls it an ‘ actionable claim.”
Also, in S. Shivnarain Laxminarain Joshi, reported in AIR 1981 SC 439, the Supreme Court has held that the word “property” is wide enough to include a ‘chose in action’.
Similarly, in Common Cause vs Union of India, reported in (1999) 6 SCC 667, the Supreme Court has held that the word “property” means the property which can be entrusted or over which dominion may be exercised as entrustment of property and this an essential ingredient of Section 405.
Section 406 I.P.C. punishes Criminal Breach of Trust with punishment of imprisonment upto 3 years, or with fine, or with both.
Section 407, which is reproduced hereunder is another specie of Criminal Breach of Trust:
“Criminal Breach of Trust by carrier, etc. – Whoever, being entrusted with property as a carrier, warfinger or warehouse-keeper, commits Criminal Breach of Trust, in respect of such property, shall be punished with imprisonment of either description for a term which may extend to seven years, and shall also be liable to fine”.
Where the Data is entrusted to a carrier, warfinger or warehouse-keeper, who commits Criminal Breach of Trust, is liable to be punished with imprisonment of upto 7 years with fine.
In so far as Data Criminals from amongst employees are concerned, Section 408 I P C, which is as follows, should be used as a strong weapon of deterrence, since punishment extends to imprisonment of 7 years with fine.
“Criminal Breach of Trust by clerk or servant – Whoever, being a clerk or servant or employed as a clerk or servant, and being in any manner entrusted in such capacity with property, or with any dominion over property, commits Criminal Breach of Trust in respect of that property, shall be punished with imprisonment of either description for a term which may extend to seven years, and shall also be liable to fine.”
Section 409 is a specie of Criminal Breach of Trust by a merchant and others which entails a punishment of imprisonment extending to life or 10 years, with fine. Section 409 reads as under:-
“Criminal Breach of Trust by public servant, or by banker, merchant or agent.- Whoever being in any manner entrusted with property, or with any dominion over property in his capacity of public servant or in the way of his business as a banker, merchant, factor, broker, attorney or agent, commits Criminal Breach of Trust in respect of that property, shall be punished with imprisonment for life, or with imprisonment of either description for a term which may extend to ten years, and shall also be liable to fine.”
Section 409 should be activated against Data Criminals from amongst the independent contractors (Call Centres etc.) to whom Data may be entrusted in the course of business for carrying out specific tasks / assignments.
It is suggested that the Agreements with employees and independent contractors ( Call Centres etc. ) should clearly stipulate an entrustment of Data to them, during the course of employment or business, as the case may be.
The issue of criminal liability of a Company and its’ Principal Officers under the Indian Penal Code, 1860 and other Laws, has agitated the minds of Courts and Jurists for a long time. Recently, the Supreme Court in Standard Chartered Bank vs Directorate of Enforcement, reported in (2005) 4 SCC page 530, inter-alia, has held that ‘the generally accepted modern rule is that except for such crimes as a corporation is held incapable of committing by reason of the fact that they involve personal malicious intent, a corporation may be subject to indictment or other criminal process, although the criminal act is committed through its agents.’
The Supreme Court has also held as follows:-
“We do not think that there is a blanket immunity for any company from any prosecution for serious offences merely because the prosecution would ultimately entail a sentence of mandatory imprisonment. The corporate bodies, such as a firm or company undertake a series of activities that affect the life, liberty and property of the citizens. Large-scale financial irregularities are done by various corporations. The corporate vehicle now occupies such a large portion of the industrial, commercial and sociological sectors that amenability of the corporation to criminal law is essential to have a peaceful society with stable economy.”
The Supreme Court in Radhey Shyam Khemka & Anr vs State of Bihar, reported in (1993) 3 SCC 54, has held that the persons managing the affairs of a Company cannot use the juristic entity and corporate personality of the Company as a shield to evade themselves from prosecution for offences under the Indian Penal Code. The Supreme Court also held as follows:-
“It need not be impressed that for prosecution for offences under the Penal Code the complainant has to make out a prima-facie case against the individuals concerned, regarding their acts and omissions which constitute the different ingredients of the offences under the Penal Code. It cannot be overlooked that there is a basic difference between the offences under the Penal Code and acts and omissions which have been made punishable under different Acts and statutes which are in nature of social welfare legislations. For framing charges in respect of those acts and omissions, in many cases, mens rea is not an essential ingredient; the concerned statute imposes a duty on those who are in charge of the management, to follow the statutory provisions and once there is a breach or contravention, such persons become liable to be punished. But for framing a charge for an offence under the Penal Code, the traditional rule of existence of mens rea is to be followed.”
Following the aforesaid legal principles, Call Centre Companies and the Principal Officers, could be implicated for Data Crimes.
Since a Company, being a juristic entity, cannot suffer corporal punishment, on conviction under I.P.C., 1860, a fine could be imposed on it. For making the Promoters / Directors / Principal Officers liable under I.P.C., 1860, their respective roles in the commission of the offence would need to be proved. They would not be automatically liable upon conviction of the Company, as there is no provision in I.P.C., 1860 as Section 85 of I.T. Act, 2000.
The offence of Criminal Breach of Trust, species of which are stipulated under Sections 405 – 409 I.P.C. as aforesaid, are cognizable and non-bailable offences, meaning thereby that the police is under a legal duty to investigate these offences and prosecute the accused, who do not have a right to bail but have to apply for bail which may or may not be granted by the Court, depending upon a confluence of factors. In Delhi, there is a special branch of Delhi Police, exclusively handling cases of Criminal Breach of Trust. Further, the complainant can directly move the Court with a criminal complaint in writing under Section 190 read with Section 200 of Code of Criminal Procedure, 1973.
Traps:
There is no bar under the law against the use of traps in the form of decoy customers etc. Traps are generally used in cases under the laws on drugs, prostitution and corruption. Though, there is no bar against the use of traps to catch the criminals, the evidence so collected with the use of traps, can be used only as supportive and corroborative evidence. The evidence collected by the use of traps cannot be made the sole-basis for conviction. Hence, traps can be used to catch and deter Data Criminals, as supportive evidence. Collecting evidence through trap witnesses in the form of decoy customers, cannot replace evidence of the actual crime committed.
The following observations of the Supreme Court in Som Prakash vs State of Delhi, reported in (1974) 4 SCC 84, are apposite in this regard:-
“6. Yet, the contentions have been ingeniously and hopefully presented. The basic attack has been on the morally murky mechanism of criminal trap. Who has not – our legends say, even rishis have – succumbed to attractive temptation in loneliness laid? And Courts have frowned upon evidence procured by such experiments since the participants are prone to be over-anxious and under-scrupulous and the victims are caught morally unawares. Even so, there are traps and traps. Where you intercept the natural course of the corrupt stream by setting an invisible contraption, its ethics is above board. On the contrary, to test the moral fibre of an officer whose reputation is suspect, if you lay a crime ‘mine’ which explodes when he, in a weak moment, walks on it the whole scheme is tainted. Of course, our social milieu is so vitiated by a superstitious belief that any official can be activised by illegal gratification, so confidential is the technique of give and take in which the white collar offender is adept and so tough is the forensic problem of proof beyond reasonable doubt by good testimony in this area, that the only hope of tracking down the tricky officers is by laying traps and creating statutory presumptions. Even Kautilya has stated that “just as fish moving under water cannot possibly be found out either as drinking or not drinking water so government servants cannot be found out while taking money”. Ex cathedra condemnation of all traps and associate witnesses is neither pragmatic nor just, nor is it fair to denounce all public servants indiscriminately. Judicial attitudes have to be discriminating, as has happened in this case. The High Court has, after careful study, chosen to accept the bona fides of the trap and its author Bishnoi, a senior police official of the S.P.E. (P.W.27). We cannot accede to the theory that the trapping of corrupt officials, in the usual course, is a polluted procedure.
7. The appellant has cited decisions in support of his plea that traps are tainted and trap witnesses are unworthy. The rulings do not go so far and merely indicate the need for caution and corroboration depending on the circumstances of each case. An awakened judicial conscience and an alert critical appraisal are the best tools in this process.”
I.T.Act, 2000
Some of the provisions of the I.T.Act, 2000 can also be invoked, parallel to the aforesaid provisions of I.P.C., against Data Criminals. For instance, Section 43 (b) of the I.T.Act, 2000, which is as follows, makes the Defendant liable to pay damages by way of compensation not exceeding Rs. 1 crore to the person affected.
“43. If any person without permission of the owner or any other person who is incharge of a computer, computer system or computer network,-
a) accesses or secures access to such computer, computer system or computer network;
b) downloads, copies or extracts any data, computer database or information from such computer, computer system or computer network including information or data held or stored in any removable storage medium;……….
d) damages or causes to be damaged any computer, computer system or computer network, data, computer database or any other programmes residing in such computer, computer system or computer network;
g) provides any assistance to any person to facilitate access to a computer, computer system or computer network in contravention of the provisions of this Act, rules or regulations made thereunder;
he shall be liable to pay damages by way of compensation not exceeding one crore rupees to the person so affected.”
“Computer database” has been defined as follows in Explanation (ii) to Section 43:
“computer database” means a representation of information, knowledge, facts, concepts or instructions in text, image, audio, video that are being prepared or have been prepared in a formalized manner or have been produced by a computer, computer system or computer network and are intended for use in a computer, computer system or computer network”
Section 43, therefore, imposes monetary liability on Data Criminals. The victim / Plaintiff need not struggle in the corridors of the dilatory Civil Justice System in India, to seek compensation under Section 43 of the I.T.Act, 2000.
Sections 46 & 47 of the Information Technology Act create a specialised adjudicatory mechanism to redress claims under Section 43. Sections 46 & 47 of the Information Technology Act are as follows:-
“46 Power to adjudicate: -(1) For the purpose of adjudging under this Chapter whether any person has committed a contravention of any of the provisions of this Act or of any rule, regulation, direction or order made thereunder, the Central Government shall, subject to the provisions of sub-section (3), appoint any officer not below the rank of a Director to the Government of India or an equivalent officer of a State Government to be an adjudicating officer for holding an inquiry in the manner prescribed by the Central Government.”
“47 Factors to be taken into account by the adjudicating officer. While adjudging the quantum of compensation under this Chapter, the adjudicating officer shall have due regard to the following factors, namely:-
a) the amount of gain of unfair advantage, wherever quantifiable, made as a result of the default;
b) the amount of loss caused to any person as a result of the default;
c) the repetitive nature of the default.”
An appeal against the order of the Adjudicating Authority lies before the Cyber Appellate Tribunal.
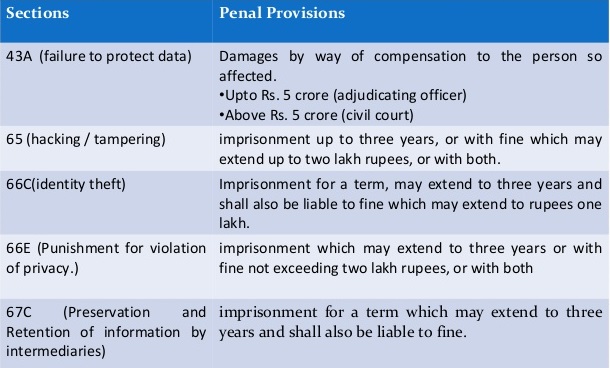
Section 66 of the I.T.Act, 2000 widely defines Hacking as follows:-
“66. Hacking with computer system.- (1) Whoever with the intent to cause or knowing that he is likely to cause wrongful loss or damage to the public or any person destroys or deletes or alters any information residing in a computer resource or diminishes its value or utility or affects it injuriously by any means, commits hacking.
(2) Whoever commits hacking shall be punished with imprisonment up to three years, or with fine which may extend upto two lakh rupees, or with both.”
Whether or not Data Criminals would be covered under the widely defined “Hacking”, as aforesaid, is a debatable question, even though, the provision is very widely worded. Whether the misappropriation and unauthorised transfer of Data amounts to diminishing the value or utility of the information residing in a computer resource, so as to bring it under the definition of Hacking, is a debatable proposition. An authoritative judicial pronouncement of this issue, by the High Court (s) or Supreme Court, would only settle the issue with some finality. Until then, Section 66 should be charged against the accused along side the various provisions of I.P.C. as stated above. The focus, however, should be on the provisions of I.P.C., 1860.
Certain Amendments have been proposed to the I.T. Act, 2000, whereby Section 66 is sought to be replaced. The proposed portion of Section 66, relevant for our purposes, is as follows:-
“a) If any person, dishonestly or fraudulently, without permission of the owner or of any other person who is incharge of a computer resource
( i) downloads, copies or extracts any data, computer data base or information from such computer resource including information or data held or stored in any removable storage medium;
he shall be punishable with imprisonment upto one year or a fine which may extend upto Rs. Two lakhs or with both;”
If the aforesaid Amendment is carried out, unauthorised data transfer etc. would become a specific offence under the I.T. Act, 2000, for which the accused if convicted, would be liable for corporal punishment. However, whether and when the said proposal becomes law, is uncertain. Hence, till then, we need to proceed on the basis of the present Section 66 of the I.T. Act, 2000.
Section 65 of the I.T. Act, 2000 punishes tampering with computer source code, which does not cover unauthorized data transfer.
Section 77 of the I T Act, which is as follows, stipulates that the penalty thereunder is not exhaustive, thereby implying in other words that other laws such as I.P.C., 1860 could be applied along with the I T Act, 2000.
“77. Penalties or confiscation not to interfere with other punishments.- No penalty imposed or confiscation made under this Act shall prevent the imposition of any other punishment to which the person affected thereby is liable under any other law for the time being in force.”
So as to enhance the credibility of the investigation into offences under the I.T. Act, 2000, the powers of investigation and arrest, have been conferred only to Police Officers not below the rank of D.S.P. and other stipulated Officers. Wide powers of arrest without warrant have been conferred under Section 80 of the I.T. Act, 2000.
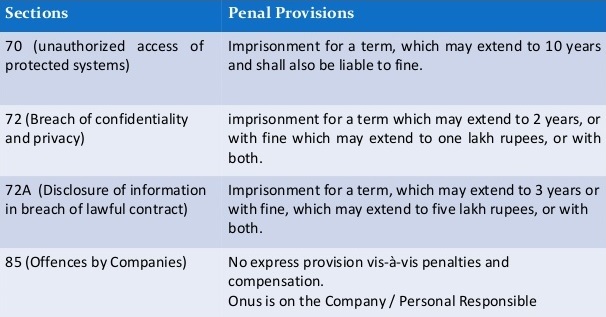
Section 85 of the I T Act, 2000 imposes criminal liability on Principal Officers of a Company accused for violations thereunder:
“85 Offences by Companies.- (1) Where a person committing a contravention of any of the provisions of this Act or of any rule, direction or order made thereunder is a company, every person who, at the time the contravention was committed, was in charge of, and was responsible to, the company for the conduct of business of the company as well as the company, shall be guilty of the contravention and shall be liable to be proceeded against and punished accordingly.
Provided that nothing contained in this sub-section shall render any such person liable to punishment if he proves that the contravention took place without his knowledge or that he exercised all due diligence to prevent such contravention.
(2) Notwithstanding anything contained in sub-section (1), where a contravention of any of the provisions of this Act or of any rule, direction or order made thereunder has been committed by a company and it is proved that the contravention has taken place with the consent or connivance of, or is attributable to any neglect on the part of, any director, manager, secretary or other officer of the company, such director, manager, secretary or other officer shall also be deemed to be guilty of the contravention and shall be liable to be proceeded against and punished accordingly.”
The Copyright Act,1957
The definition of “literary work” under Section 2(o) of the Copyright Act, 1957 includes tables and Computer Databases. Infringement of Copyright is defined under Section 51 of the Act. Infringement of Copyright is also a criminal offence under Section 63.
Section 69 of the Copyright Act , 1957, like Section 85 of the I.T.Act, 2000, makes the Principal Officers of the Company committing an offence, also liable for criminal prosecution. Offences under Section 63 of the Copyright Act , 1957 are also cognizable and non-bailable.
Amendments Information Technology (Amendment Act) 2008:
a) Vide Section 43A and 72A, protection of sensitive personal information and data has been included.
b) Maintenance of reasonable security practices and procedures
c) civil and criminal liabilities
Following amendment of I.T. Act in 2008, the following provisions have become effective:
Section 66B. Punishment for dishonestly receiving stolen computer resource or communication device.- Whoever dishonestly receives or retains any stolen computer resource or communication device knowing or having reason to believe the same to be stolen computer resource or communication device, shall be punished with imprisonment of either description for a term which may extend to three years or with fine which may extend to rupees one lakh or with both.
Section 66-C Punishment for identity theft. (Inserted Vide ITA 2008)
Whoever, fraudulently or dishonestly make use of the electronic signature, password or any other unique identification feature of any other person, shall be punished with imprisonment of eitherdescription for a term which may extend to three years and shall also be liable to fine which may extend to rupees one lakh.
Strategies For Data Protection:
a) Agreement(s) with an employee must contain suitable clauses by which Data / Confidential Information ( as defined in the Agreement ) is entrusted by the employer/company to the employee;
b) The entrustment of Data, should also be clearly stipulated in the Agreement(s) with employees and other independent contractors so as to effectively deter Data Criminals and they should be made responsible to ensure that Data Crimes are not committed.
c) Confidentiality clauses should be incorporated
“Since information by itself is not tangible by nature, the relationship of trust with respect to the information including confidential information under entrustment to the employee at any point during the course of his employment, shall continue even after the employee leaves the employment of the Company and after returning or delivering the tangible medium containing confidential information”
d) Employees should be held liable for “misusing confidential information or using the same for any personal use or use, other than strictly for performing duties in the course of employment with the Company”.
e) Employees should give an undertaking not to do any act of commission or omission which is in breach of trust or contract, including sell, transfer, send, give access to any person, remove, move, copy, disclose, take back-ups or use the same, other than in the manner as specifically authorised by the Company”.

One reply on “Data Theft and Data Protection Precautions in India”
Never heard of a steam shower enclosure up until I discovered
this website, so glad I did so really want one right away
and finance letting will likely be owning one soon enough
LikeLike